The Journey to Cybersecurity Maturity
From executive boardrooms to the heart of server room operations, the call for strong cybersecurity measures saturates every level and function within modern organizations. But, as cybersecurity experts, we understand that cybersecurity maturity involves more than just strengthening defenses and applying security patches.
The journey towards cybersecurity maturity is a multifaceted endeavor, one that seamlessly blends leadership, governance, risk management, compliance, and strategic partnerships. Through these strategies, Chief Information Security Officers (CISOs) and cybersecurity leaders can start their journey to cybersecurity maturity that ensures compliance and promotes a state of resilience, growth, and long-term success.
Characteristics of Effective Leadership
As organizations navigate the complexities of cybersecurity maturity, the role of the CISO becomes increasingly vital. The work of CISOs goes beyond just managing security; it requires visionary leadership, advocating at the board level, empowering teams, and having a strategic outlook.
The objective is straightforward: guide the company towards cybersecurity maturity with visionary leadership, board-level advocation, empowering teams and cultivating a culture of vigilance, strategic planning, and communicating with transparency.
Visionary Leadership
Guiding the company towards cybersecurity maturity requires visionary leadership. A visionary CISO doesn’t merely react to threats; they proactively shape the organization’s security landscape. They chart a course toward a future where cybersecurity is not a limitation but a powerful motivation for achieving business objectives. Their foresight anticipates challenges, positioning the organization ahead of potential risks.
Advocating at the Board Level
The modern CISO serves as a crucial bridge between cybersecurity’s technical intricacies and the boardroom’s strategic objectives. They are experienced at translating complex security concepts into tangible business impacts, garnering support and resources from board members. By highlighting how critical it is to invest in cybersecurity, they ensure that the organization remains resilient in the face of threats and grows toward cybersecurity maturity.

Empowering Teams and Cultivating a Culture of Vigilance
A proactive CISO recognizes that cybersecurity maturity is a collective effort. They empower their teams with security awareness programs, knowledge, resources, and a culture of vigilance. By fostering an environment of continuous learning and skill development, they can cultivate a workforce that is proactive in identifying and mitigating risks.
Strategic Planning to Align Objectives with Business Goals
The journey to cybersecurity maturity requires a strategic CISO who is familiar with the intricacies of the business. They should align every cybersecurity initiative with the broader organizational strategy. By setting clear, actionable goals, they can ensure that cybersecurity efforts are not isolated but seamlessly integrated into the heart of the organization.
Transparent Communication
Guiding an organization toward cybersecurity maturity needs a CISO who can communicate with clarity, honesty, and inspiration. They should foster a culture of open dialogue where every member of the organization understands their role in safeguarding critical assets. This transparency builds trust, enabling a collective commitment to cybersecurity excellence.
We know a holistic cybersecurity strategy demands time and deep expertise. If you’re not sure where to begin, let Edge Networks simplify your cybersecurity journey. Our vCISO is here to streamline the process for you. Partner with us and tap into top-tier security leadership, turning challenges into collaborative solutions.
The Role of Cybersecurity Frameworks
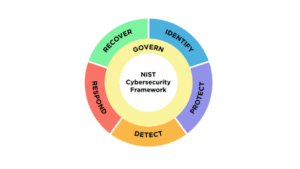
When it comes to cybersecurity maturity, having a structured framework to rely on ensures that organizations can navigate the complex realm of security with clarity and confidence. A skilled CISO recognizes the significance of aligning security efforts with broader business goals, using frameworks as a guide to harmonize security measures with the overall organizational strategy. The National Institute of Standards and Technology’s Cybersecurity Framework (NIST CSF) serves as a great guide in establishing a solid cybersecurity program. This framework provides a comprehensive structure for managing and mitigating cybersecurity risks and can help meet various compliance requirements, including SOC2 and ISO frameworks.
From NIST CSF to Compliance and Beyond
What sets the NIST CSF apart is its versatility. Beyond its primary function of setting up a cybersecurity program, it seamlessly aligns with other compliance requirements.
By emphasizing the core functions of Identify, Protect, Detect, Respond, Recover, and Govern, the NIST CSF serves as a roadmap for developing a comprehensive cybersecurity strategy. Its flexibility ensures that it can be tailored to meet the unique needs of any organization. Whether you’re navigating the complexities of regulatory compliance or safeguarding against emerging threats, the NIST CSF provides a solid foundation to build on.
Governance, Risk Management, and Compliance Platforms
Governance, Risk Management, and Compliance (GRC) play a pivotal role in improving cybersecurity maturity by providing a structured framework and holistic approach to managing and mitigating cybersecurity risks.
Transitioning from traditional, spreadsheet-based cybersecurity management to a Governance, Risk Management, and Compliance (GRC) model marks a significant leap forward in how organizations safeguard critical assets. GRC empowers them with a centralized, automated, and real-time monitoring solution that effectively enhances their ability to manage cybersecurity risks and compliance requirements.
GRC serves as a strategic toolset that contributes to the overall cybersecurity posture of an organization in several key ways:
- Centralization and Consolidation: GRC activities are brought under one roof, streamlining operations and ensuring a cohesive approach to cybersecurity. This shift from scattered spreadsheets to a unified platform offers a holistic view of an organization’s cybersecurity posture. It streamlines operations, reduces redundancy, and seamlessly integrates all aspects of governance, risk, and compliance.
- Automation for Efficiency: Routine tasks are automated and more efficient, which frees up valuable resources for strategic initiatives. It minimizes the potential for human error, significantly improving the overall effectiveness of cybersecurity management efforts.
- Scalability: As organizations grow, so do their cybersecurity needs. A GRC platform is designed to scale alongside the organization’s expansion. This growth inevitably leads to increased complexity and volume of digital assets to protect.
- Real-time Monitoring: Immediate insights into the health of your cybersecurity posture enable timely responses to potential threats or vulnerabilities. This heightened responsiveness ensures potential risks are identified and addressed swiftly, minimizing potential damage and safeguarding critical assets.
- Advanced Reporting and Metrics: Clear, concise reporting provides a comprehensive view of progress and areas that may require additional attention. This enables stakeholders at all levels of the organization to grasp the current situation from the overall risk landscape to the effectiveness of specific security measures.
Incorporating GRC into your cybersecurity strategy strengthens your compliance efforts and equips you with a dynamic toolset to effectively manage risks and level up your cybersecurity maturity.

Strategic MSSP Partnerships for Enhanced Security
As organizations strive to protect their digital assets and advance toward cybersecurity maturity, partnering with a Managed Security Service Provider (MSSP) is a strategic move. MSSPs offer a wealth of resources and expertise, and their collaborative approach can be a game-changer in strengthening an organization’s defenses. There are many benefits of an MSSP partnership, such as:
Industry Insights
Partnering with a Managed Security Service Provider (MSSP) can propel an organization toward establishing a strong cybersecurity program. Their industry insights, cultivated through years of hands-on experience, give organizations a crucial edge. They’re familiar with emerging attack vectors, tactics, and vulnerabilities that may not be apparent to others within the organization.
Cutting-Edge Technologies
MSSPs are at the forefront of adopting and deploying cutting-edge cybersecurity technologies. They’re on top of the latest advancements in threat detection, incident response, and security infrastructure, which ensures organizations benefit from the most up-to-date and effective tools in the fight against cyber threats.
Incident Response
MSSPs are equipped with reliable incident response plans and protocols. These established procedures, enhanced through real-world experiences, enable organizations to react promptly and decisively in the event of a cyber incident. This readiness significantly reduces a security breach’s potential impact and associated costs.
Threat Detection
MSSPs also excel in the realm of threat detection. Leveraging advanced tools, analytics, and threat intelligence, they continuously monitor for indicators of compromise and suspicious activities. This proactive approach allows for the early identification of potential threats, often intercepting attacks before they can inflict substantial harm.
Customized Risk Assessments and Mitigation Strategies
Every organization has its unique risk profile, influenced by factors such as industry, regulatory environment, and technology stack. MSSPs recognize this diversity and employ tailored risk assessments to pinpoint vulnerabilities specific to each organization. These assessments serve as the foundation for developing customized threat mitigation strategies. By addressing vulnerabilities in a targeted manner, organizations can maximize the effectiveness of their cybersecurity efforts.
Enabling Growth and Adaptation
As organizations grow and evolve, so do their cybersecurity needs. MSSPs have the flexibility and scalability to evolve alongside their clients. Whether expanding operations, integrating new technologies, or entering new markets, MSSPs ensure that the cybersecurity program remains aligned with organizational objectives.
By leveraging the MSSP’s industry insights, technological expertise, incident response capabilities, and customized risk assessments, organizations can strengthen their defenses and proactively navigate the complex cybersecurity landscape.

Ensuring an Effective MSSP Collaboration
Collaborating with a Managed Security Service Provider (MSSP) is a strategic move, but its success hinges on careful planning and execution. To maximize the benefits of this partnership, organizations should adhere to a set of best practices:
- Clearly Outline Objectives and Expected Outcomes: Transparency is essential in any successful collaboration. Clearly defining the objectives and expected outcomes of the MSSP partnership sets the stage for a unified vision. This clarity ensures that both parties are aligned and working towards a common goal. It also provides a clear benchmark against which progress can be measured.
- Set Up Structured Communication Protocols: Establishing structured communication protocols ensures that information flows seamlessly between the organization and the MSSP. This includes regular status updates, incident reports, and strategic discussions. Clear lines of communication foster trust, enable quick decision-making and enhance the overall effectiveness of the cybersecurity program.
- Regularly Review Performance Against SLAs: Service Level Agreements (SLAs) serve as the contractual framework for the MSSP partnership. They outline the expected level of service, response times, and performance metrics. Regularly reviewing performance against these agreed-upon benchmarks is crucial. It allows organizations to assess whether the MSSP is meeting expectations and provides an opportunity to address any areas for improvement.
- Develop a Future-Focused Plan for Building In-House Capabilities: While an MSSP provides invaluable expertise and resources, organizations should also have a long-term strategy for building in-house cybersecurity capabilities. This forward-looking plan ensures that the organization progressively enhances its internal cybersecurity proficiency. It may involve hiring and training internal security personnel or gradually transitioning specific security functions in-house.
Organizations can optimize their collaboration with an MSSP by adhering to these best practices. This approach ensures that the partnership remains productive and aligned with organizational objectives and lays the groundwork for a cybersecurity program that can evolve and adapt alongside the organization’s growth.
Transitioning to a Dedicated Security Team
Recognizing when the time is right to establish an in-house security team is a critical milestone in an organization’s cybersecurity journey. Edge Networks is dedicated to guiding companies through this transition. We help identify key indicators that signal readiness, such as the complexity of security needs, the scale of operations, and the increasing volume of sensitive data being managed. These signs serve as clear markers that an internal security team is not only beneficial but essential for safeguarding the organization’s digital assets effectively.
Building a cybersecurity team in-house requires a strategic roadmap. Just hiring someone and telling them you are now on the security team isn’t enough in 2023. Edge Networks will guide you through the process of identifying who to hire first, how to manage them, how to provide vision to them, and what they will be doing clearly with our “day in the life of” examples and standard operation procedures.
Take the Next Step in Your Journey
Achieving cybersecurity maturity takes effort and a strategic approach that goes beyond technical measures. From visionary leadership and strategic planning to adopting frameworks like NIST CSF and embracing GRC solutions, each step propels the journey. Collaborating with MSSPs unlocks industry insights and advanced technologies, strengthening defenses. Effective partnerships, guided by transparency and structured communication, pave the way for success.
As organizations evolve, so should their cybersecurity capabilities, whether through optimized MSSP collaborations or the establishment of a dedicated in-house security team, Edge Networks stands ready to navigate this shift strategically. Your organization’s cybersecurity maturity is our shared goal. Contact us today to learn more.