It’s no secret that smart homes are becoming more and more popular. For many, a smart home helps make life a little easier and even feel more luxurious, whether it’s a Google Home being used as a speaker to stream your favorite songs across the house, a Ring doorbell keeping track of who’s on your doorstep, or an Amazon Alexa automating tasks around your home. Consumers have access to a growing range of IoT appliances, including smart refrigerators, lightbulbs, coffee makers, and even washing machines, proving that there is something for everyone in the smart home device realm.
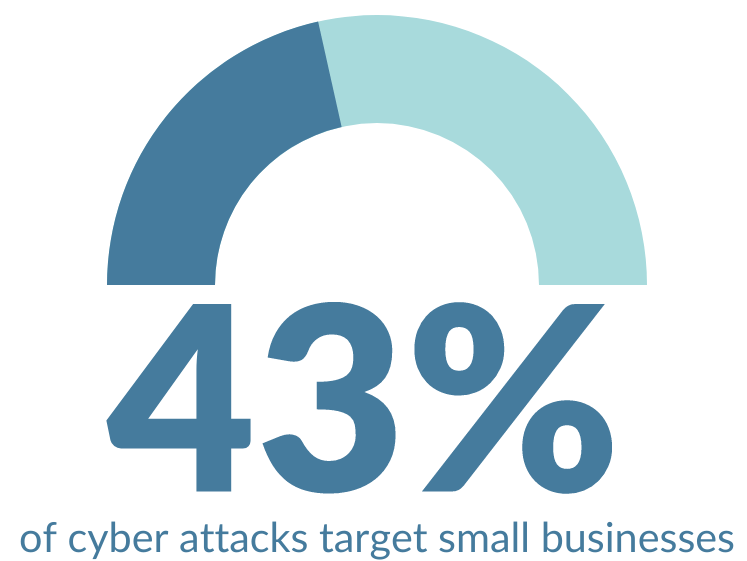
While this technology offers many benefits, it also comes with a risk: cybersecurity threats. Because the smart device market is expanding quickly, it has become a fast-growing target for hackers. In the first half of 2021 alone, there were more than 1.5 billion attacks on smart devices, with attackers generally looking to steal data or use compromised devices for future breaches and cryptocurrency mining. If proper precautions aren’t taken, your smart home devices can be vulnerable to data breaches too.
In this blog post, we will discuss what smart home breaches are, what to do if your device is compromised, how businesses can be affected, and how to prevent these breaches.
What is a Smart Home?
A smart home is a home that uses internet-connected devices to automate tasks like lighting, security, temperature control, and more. These devices are often controlled by a mobile app or voice assistant such as Amazon Alexa or Google Home. While smart homes offer many conveniences, they also create new opportunities for cybercriminals to creep into your home.

What is a Smart Home Breach?
A smart home breach is when an unauthorized user gains access to your smart home devices or network. This can happen in a number of ways; here are a few of them.
Unsecured Wi-Fi networks and Bluetooth connections
Unsecured Wi-Fi networks and Bluetooth connections leave your home vulnerable to attack. If a hacker gains access to your smart home, they can steal your personal data, spy on you, or even control your devices remotely.
By exploiting vulnerabilities in smart home devices, hackers can gain access to your network and steal your data. This type of attack is especially concerning because it can happen without the homeowner ever knowing that their security has been compromised
Malicious Apps
These breaches can often occur through malicious apps. There are many smart devices that can be controlled by mobile apps. However, there are also many malicious apps that masquerade as legitimate smart home apps. These malicious apps can give attackers access to your smart home devices and data.
Phishing Attacks
Attackers will send you an email or text message that appears to be from a legitimate company, such as your smart home manufacturer or service provider. The message will likely contain a link that takes you to a fake website where you are prompted to enter your personal information, such as your username and password. Once the attacker has this information, they can gain access to your smart home devices and data.
What Should You Do if a Smart Home Breach Occurs?
Change Passwords
Change the passwords for all of your online accounts, especially any that are linked to your smart home devices. This includes your email, social media, and any other accounts that might be connected to your smart home in some way. It’s also a good idea to keep an eye on your credit report and bank statements for any suspicious activity.If you notice anything out of the ordinary, be sure to report it to the proper authorities.
Factory Reset Your Devices
If you’re really worried about someone gaining access to your smart home devices, you can always factory reset them and start from scratch. While this may be a hassle in the short-term, it’s worth it if it means protecting your data and keeping your family safe.
Report the Incident
Reach out to your smart home’s customer support line and let them know what happened. They may be able to help you troubleshoot the issue and prevent it from happening again in the future. They may also have additional steps for you to take or may be able to help you remotely disable any malicious functionality that has been added to your devices.

How to Prevent Smart Home Breaches?
Reach out to your smart home’s customer support line and let them know what happened. They may be able to help you troubleshoot the issue and prevent it from happening again in the future. They may also have additional steps for you to take or may be able to help you remotely disable any malicious functionality that has been added to your devices.
Create Strong Passwords for Your Smart Devices
Setting a strong password for your smart device and your network can help keep your data safe and secure.
Use a Private Wi-Fi Network to Connect to Your Smart Home
You should also avoid using public Wi-Fi networks to connect to your smart home as these are often unsecure. Public wifi networks are often unencrypted, which means that anyone can listen in on the data being sent back and forth. This includes passwords, credit card information, and more. Ideally, you would use a private Wi-Fi network with a strong password. If you must use public Wi-Fi, make sure to use a VPN (virtual private network) to encrypt your data.
Update Your Device’s Software Regularly
To help combat breaches, it’s important to keep your smart devices’ software up-to-date. Manufacturers often release updates that patch security vulnerabilities, so by keeping your software updated, you’re helping to protect yourself from potential breaches and closing any potential security holes that could be exploited by malicious actors.
How Can Smart Home Breaches Affect My Business?
If you’re a business owner, it’s important to be aware that smart home breaches can affect you as well. For example, if an employee’s smart home is breached, the attacker could gain access to sensitive company data. To prevent this from happening, businesses should have strict cybersecurity policies in place, and employees should be trained on how to keep their smart devices secure.
If your business uses smart devices around the office, it’s important to take the right precautions to avoid a smart device breach. Make sure that all smart devices are password-protected and that only authorized employees have access to them. You should also have a cybersecurity plan in place in case of a breach. This plan should include steps for how to identify and fix the issue, as well as how to prevent future breaches from happening. You should also prioritize educating your employees on smart device security and best practices, as well as how to respond if a breach does occur.
How a Managed IT Service Provider Can Help
If you’re not sure where to start, a managed IT service provider can help you create and implement a cybersecurity plan. They can also provide guidance on smart device security and help you troubleshoot any issues that arise.
Contact us today to learn more about how we can help keep your business and home safe from breaches.